Here is where I’m at:
My computer is apparently able to choose on which nodes of a network to act, to best contain an infection from spreading across a network, within preset constraints.
One image (or one like it) could well be the conclusion of the first part of my dissertation:
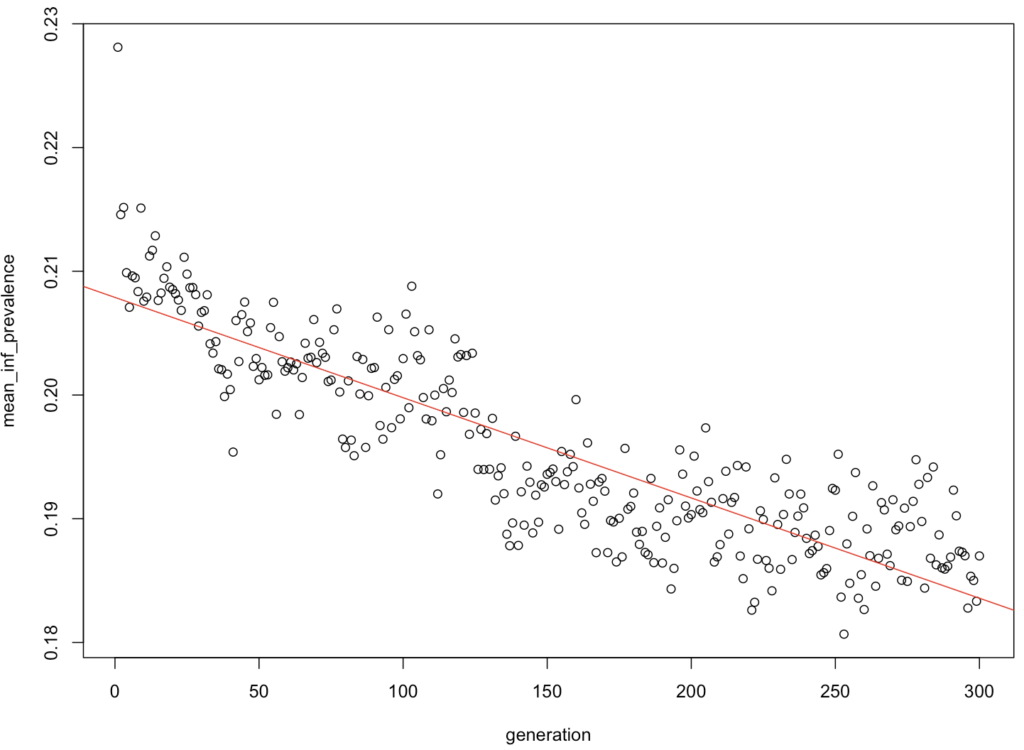
Many validations and long runs (it takes 4-5′ per run, on a small network…) to go for now, with varying variables and constraints, but if all goes well along the next few days, I shall be able to begin analyzing the results, which is the interesting part to generalize conclusions (if at all possible).
And then, part 3, I will go back to the concept board and focus on applying the conclusions (if any) to the Cybersecurity Operations domain.
I’m ecstatic, right now!